What is TLS?#
Transport Layer Security (TLS) is a cryptographic protocol that provides privacy and data security for communication over the internet. TLS is the successor to SSL (Secure Sockets Layer) and is primarily used to encrypt communication between web applications and servers.
If you’ve ever made a purchase online using your credit or debit card, the communication between your browser and the server for this transaction was almost certainly protected by TLS.
While this example highlights one common use case, TLS applications extend far beyond online purchases. TLS is most used to secure HTTP transactions, but since it operates over TCP, it can also be used by other applications that rely on TCP for communication, such as email protocols (SMTP, IMAP, POP3), and even Voice over IP (VoIP) communications.
TLS was first proposed by the Internet Engineering Task Force (IETF) in 1999 with RFC 4346, and the most recent version, TLS 1.3, was published in 2018.
How TLS works?#
To better understand how TLS secures communication, we can break down its operation into three key phases: Handshake, Key Derivation, and Data Transfer.
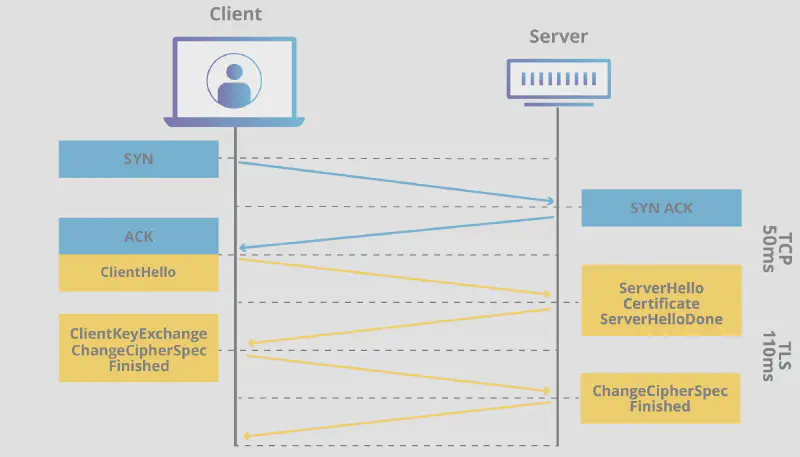
Handshake:#
The handshake process is the first step in establishing a secure connection between the client (e.g., your browser) and the server. During this phase, both parties agree on cryptographic algorithms and exchange keys.
- ClientHello: The client sends a “hello” message to the server, which includes supported cryptographic algorithms and a randomly generated number.
- ServerHello: The server responds with its choice of algorithm, its certificate (to prove its identity), and its own random number.
- Authentication and Pre-Master Secret: If the client trusts the server’s certificate, it encrypts a pre-master secret using the server’s public key and sends it to the server. Only the server can decrypt this secret with its private key.
Key Derivation#
Once both parties have exchanged the premaster secret, they use this value along with the random numbers exchanged during the handshake (client random and server random) to derive the master secret. From the master secret, the client and server generate the symmetric keys, message authentication codes (MAC) keys, and sometimes Initialization Vectors (IVs) for certain encryption modes. These keys will be used to encrypt, decrypt, and authenticate the actual data, ensuring confidentiality and integrity for the duration of the session.
Data Transfer#
With the handshake and key derivation complete, secure data transfer can begin. All further communication between the client and server is encrypted using the symmetric key. TLS ensures not only encryption but also integrity, using MACs or Authenticated Encryption with Associated Data (AEAD) to detect tampering and prevent unauthorized modifications.
At the end of the session, both the client and server can agree to terminate the connection, clearing the session keys to prevent reuse in future sessions, which helps maintain forward secrecy if supported (e.g., with ECDHE key exchange).
Deeper dive into Handshake#
TLS does not mandate the use of specific symmetric or asymmetric algorithms; instead, it allows the client and server to negotiate and agree on cryptographic algorithms at the beginning of the session. The detailed steps of the TLS handshake are as follows:
- ClientHello: The client sends a list of supported cryptographic algorithms (cipher suites), including symmetric ciphers (like AES or ChaCha20), key exchange methods (like RSA or ECDHE), and MAC algorithms. The client also sends a random value, called the client nonce (or client random).
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384ServerHello: The server selects a cipher suite from the client’s list, specifying the symmetric algorithm (e.g., AES), the public key algorithm (e.g., RSA or ECDHE), and the MAC algorithm (e.g., HMAC-SHA256). The server also sends its digital certificate containing its public key, and a server nonce (server random).
Certificate Verification: The client verifies the server’s certificate, ensuring it was issued by a trusted Certificate Authority (CA) and that it matches the server’s identity. The client then extracts the server’s public key from the certificate.
Pre-Master Secret Exchange:
- In RSA key exchange, the client generates a premaster secret, encrypts it with the server’s public key, and sends it to the server.
- In ECDHE (Elliptic Curve Diffie-Hellman Ephemeral) key exchange, the client and server exchange Diffie-Hellman parameters to securely compute a shared premaster secret without directly transmitting it over the network.
In modern TLS versions (like 1.3), RSA key exchange is deprecated in favor of ephemeral Diffie-Hellman methods, which provide forward secrecy.Master Secret Generation: Both the client and server use the premaster secret along with the client and server random values to compute the master secret. From the master secret, they independently derive the symmetric encryption keys, MAC keys, and IVs (if needed). These keys are used for encrypting and authenticating the session data.
Finished Messages:
- The client sends a Finished message, containing a MAC of all handshake messages up to this point, encrypted with the new symmetric key.
- The server also sends a Finished message, similarly, containing a MAC of the handshake messages.
Secure Communication: Once the Finished messages are successfully exchanged, the handshake is complete, and secure data transfer can begin. All further messages are encrypted and authenticated using the negotiated cipher suite.
Summary:#
TLS provides a robust and widely used method for securing communication across the internet. By utilizing a combination of encryption, integrity verification, and authentication, TLS ensures that data is protected from interception, tampering, and unauthorized access. Understanding the TLS handshake and how keys are derived helps clarify why it’s such a critical protocol for internet security today.




